The Scenario
Necessity is the mother of invention. What if your WSUS isn’t working correctly, SCCM’s SUP is failed, or you just really need to get around them to install patches during OSD? In this post I’ll guide you through the process to go straight to Microsoft for updates during OSD.
Things I Tried That Failed
I manually created the client record for other reasons and I tried adding the client record to the collections where patches were deployed. But while the machine saw and evaluated the updates it only reported at the end 0x0 – no actionable updates to install. Updates *must* be deployed to the same collection where the OSD TS deployment resides. Bummer.
I tried removing the WindowsUpdate registry items to allow it to look at Microsoft, then force a UsoClient.exe startscan, but that only works once you’re in the GUI and the old faithful wuauclt.exe has been deprecated in Server 2016.
What Actually Worked
Finally, I found a Petri article that pointed me to the magic grits (probably from the same place “that sold Jack his beanstalk beans”). It was this handy little module that enabled me to achieve my goal. With a little tinkering I was able to write a PowerShell script that will use the module to download and install patches during OSD. I suggest you read the Petri article to get a feel for what it can do, and definitely read the help files once you have it imported, but I’ll show you my code and what I did to get you started.
The Script Itself
Here’s how I scripted the process.
Import-Module PSWindowsUpdate #Clear Windows Update registry items Set-ItemProperty HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate -Name DisableDualScan -value "0" Set-ItemProperty HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate -Name WUServer -Value $null Set-ItemProperty HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate -Name WUStatusServer -Value $null #Add ServiceID for Windows Update Add-WUServiceManager -ServiceID 7971f918-a847-4430-9279-4a52d1efe18d -Confirm:$false #pause and give the service time to update Start-Sleep 30 #Scan against Microsoft, return list of software (as opposed to driver) updates Get-WUInstall -MicrosoftUpdate Software -ListOnly #Hide unwanted updates here - replace # sign with appropriate information. Read help files for the full extent Hide-WindowsUpdate -KBArticleID "KB#######" -Confirm:$false Hide-WindowsUpdate -Title "###some update text###" #optional Hide-WindowsUpdate -UpdateType Driver -Confirm:$false #Now install the updates and do not autoreboot - we always want sccm to coordinate reboots Get-WUInstall -MicrosoftUpdate Software -AcceptAll -IgnoreReboot
As you can see there are multiple filter values and you can replicate the same approval rules you may have on WSUS/SCCM. The registry entries will repopulate on the next reboot when the configmgr client initializes. You can watch the resource manager reach out to Microsoft during the scan and download patches.
Creating the Package
First we have to create a package containing the PS module folder (extracted from zip file) and script and distribute it to our DPs accessed for OSD. In our task sequence we need a couple of steps to:
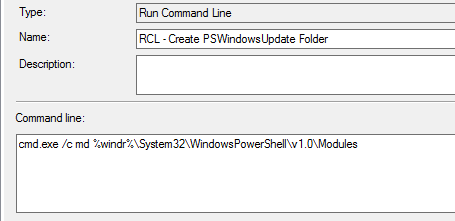
1) Create the destination copy folder, PSWindowsUpdate in: %windir%System32\WindowsPowerShell\v1.0\Modules
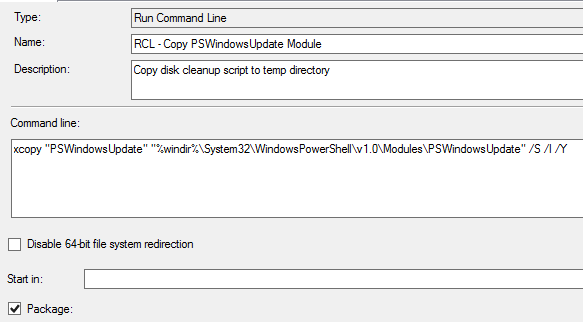
2) xcopy the PSWindowsUpdate module contents to that path
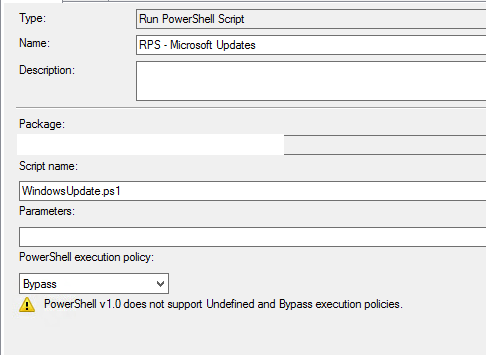
3) We need a step to run the script, so we use the built-in Run PowerShell Script step, tell it to use our package, then run the script. Don’t forget to set the execution policy to bypass!
4) Then add a reboot step after this and make sure to boot back into the currently installed OS.
And that’s basically it. To validate during OSD hit the F8 key (after this step has completed), type PowerShell, hit enter, then type get-hotfix, hit enter, and check the installation dates and KB numbers. You’ll find you’ll have the latest and greatest patches, all without the need for WSUS/SCCM.
Fair Warning
Typical YMMV, perform at your own risk, don’t break company policies, test in a lab, yada yada yada. I’m not responsible if you mess something up. Good luck!
You must be logged in to post a comment.