Let’s say you have an application, server, switch, whatever, that only operates in IPv4 and you think it would be much simpler to access it over DirectAccess than firing up the old VPN connection and resetting all your active network connections. In my case I wanted to use an RDP file to access my internal vCloud lab.
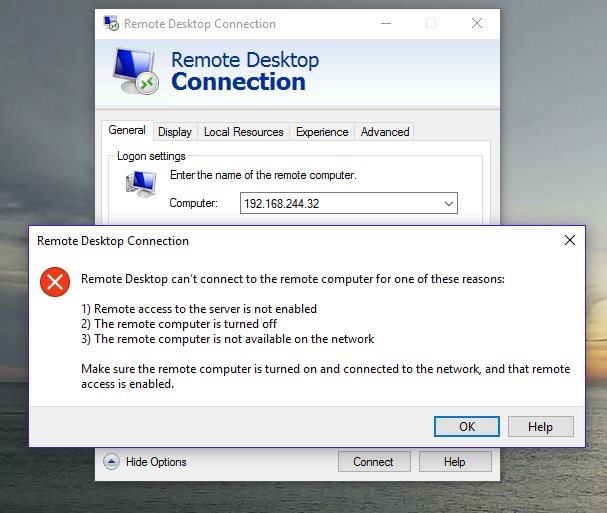
If this VM had a DNS record it wouldn’t be an issue, but since it’s a lab we don’t publish DNS records for those separate networks. That means DirectAccess cannot find it.
Furthermore, because of the way the connect to console works with Java the app breaks when routing through a firewall over DirectAccess. I could fix the firewall, but that isn’t in my purview and I don’t want to trouble my firewall guy. The goal, anyway, is simply to access my VM which is only available through an IPv4 address, but getting it to go over DirectAccess.
After a while I got the idea to translate the IP from IPv4 to IPv6. I remember doing my hexadecimal conversions way back when I was learning binary and hex math and IPv6 is hexadecimal in nature. So here’s what you need:
If you’re on DirectAccess, ping an internal resource. This will spit back an IPv6 address at you. Copy and paste everything prior to the last two quartets (one quartet is the four digits between the colons). This will be the prefix you’ll need. Specifically, you’ll need the first 6 (of 8 total) groups.
Here’s a sample IPv6 address that we’ll pretend we received from a ping to an internal resource: 3ffe:1900:4545:3:200:f8ff:fe21:67cf
Next we need to translate the IPv4 address into an IPv6 address. Each octet in an IPv4 address corresponds to two places in the IPv6 quartets, and for our purpose, we’re concerned with the last two octets.
Here’s your code for translating binary IP addresses into hexadecimal ones:
0=0 4=4 8=8 12=C
1=1 5=5 9=9 13=D
2-2 6=6 10=A 14=E
3=3 7=7 11=B 15=F
Take an internal IP address, such as 192.168.1.138. We divide each octet by 16 and look for the remainder and translate them into hex.
192/16 = 12 = C. Since there is no remainder the first two digits are C0.
168/16 = 10 = A with a remainder of 8, so the second two digits are A8. So the seventh quartet of the IPv6 address will be C0A8.
1 is less than 16, so we cannot divide it. It will be its own digit, much like 1 in a binary octet is expressed as .00000001, but in hex this will be represented in a condensed format of :01.
138 is divisible by 16, so we will divide again.
138/16 = 8 = 8 with a remainder of 10, which equals A. So our last quartet is 018A.
So let’s assume this IPv6 address is one of the internal resources of our network to which DirtectAccess connects us. If we substitute the last two quartets with our ip address we would have the value of:
3ffe:1900:4545:3:200:f8ff:C0A8:018A
If we ping 3ffe:1900:4545:3:200:f8ff:C0A8:018A, assuming the firewall is configured to pass IPv6 echo requests and replies, you will get a response. We can try RDP now:
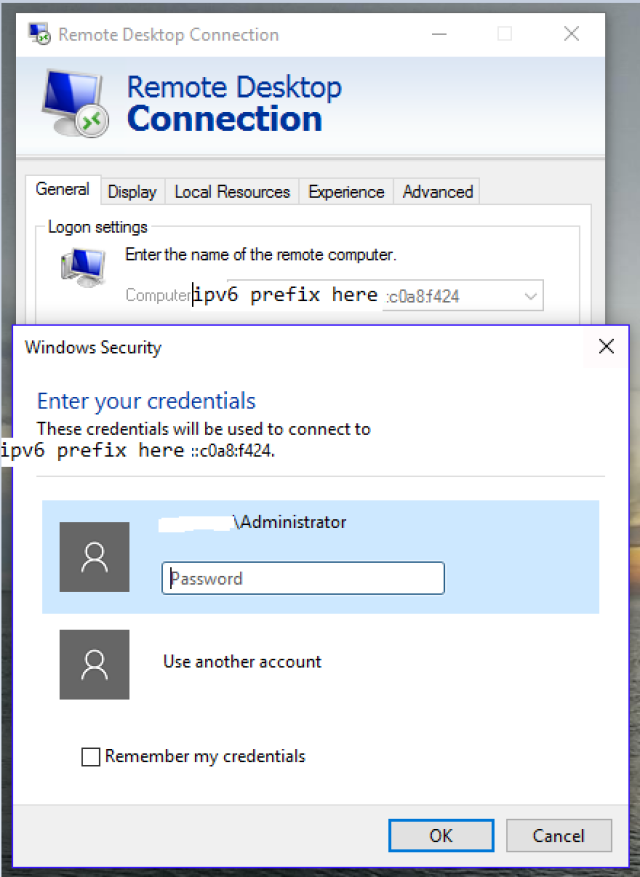
(In my scenario I need to convert the IP of 192.168.244.36. This converts to c0a8:f424.)
So why does it work and how does it know how to get there? Well, just like when you get a DHCP address in IPv4, when you get an IPv6 address from DirectAccess you will receive an IPv6 set of routes (along with the NRPT). Ultimately, networks still only use IP addresses to route traffic and this is why the traffic properly reaches its destination.
Furthermore, when you are connected to DirectAccess you will notice you have two IP routing tables when you run the route print command. Which table your machine uses depends on the type of IP returned by a DNS query. On DirectAccess your machine is configured to use an NRPT (Network Resolution Policy Table) which is a registry-based hosts file. If your search matches certain conditions, such as your internal domain namespace, your machine sends its DNS requests to the DirectAccess server. If your query does not match what is in the NRPT it routes traffic over the IPv4 network.
On the DirectAccess server the DNS6to4 adapter is the one doing the DNS translation. It makes a query against an internal DNS server and converts the IPv4 address into an IPv6 address that the client can understand. The DA server also works just like a router in that it changes the source MAC to its own so the packets can find their way back home, this is the function of the NAT6to4 adapter. It effectively strips the entire first part of the address, converts your last two quartets into their corresponding IPv4 address and passes it on to the next network hop to be routed with a unique port number.So similar to a NAT table on a firewall, the DA server keeps track of which ports it assigns correspond to which IPv6 addresses.
To be overly simplistic, DirectAccess is an IPv6 to IPv4 router. It does this each time we request a resource by hostname. But if you can’t have a DNS record for your internal resource, you can still route traffic over it by converting your IPv4 address into an IPv6 address and forcing your traffic over the IPv6 route.
Great article Wayne! Would you be open to us reposting it with attribution and link back to this post?
Absolutely. Thanks!